“Some of the uncommon components of this case was the attacker’s use of bodily entry to put in a Raspberry Pi gadget,” Group-IB Senior Digital Forensics and Incident Response Specialist Nam Le Phuong wrote. “This gadget was related on to the identical community swap because the ATM, successfully inserting it contained in the financial institution’s inner community. The Raspberry Pi was outfitted with a 4G modem, permitting distant entry over cellular knowledge.”
To keep up persistence, UNC2891 additionally compromised a mail server as a result of it had fixed Web connectivity. The Raspberry Pi and the mail server backdoor would then talk by utilizing the financial institution’s monitoring server as an middleman. The monitoring server was chosen as a result of it had entry to nearly each server throughout the knowledge heart.
The Community Monitoring Server as an middleman between the Raspberry Pi and the Mail Server.
Credit score:
Group-IB
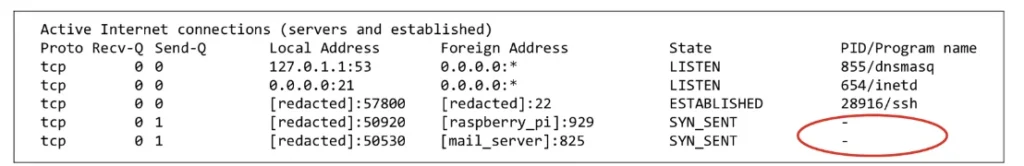
As Group-IB was initially investigating the financial institution’s community, researchers observed some uncommon behaviors on the monitoring server, together with an outbound beaconing sign each 10 minutes and repeated connection makes an attempt to an unknown gadget. The researchers then used a forensic device to investigate the communications. The device recognized the endpoints as a Raspberry Pi and the mail server however was unable to establish the method names answerable for the beaconing.
The forensic triage device is unable to gather the related course of title or ID related to the socket.
Credit score:
Group-IB
The researchers then captured the system reminiscence because the beacons have been despatched. The overview recognized the method as lightdm, a course of related to an open supply LightDM show supervisor. The method gave the impression to be legit, however the researchers discovered it suspicious as a result of the LightDM binary was put in in an uncommon location. After additional investigation, the researchers found that the processes of the customized backdoor had been intentionally disguised in an try and throw researchers off the scent.
Phuong defined:
The backdoor course of is intentionally obfuscated by the risk actor by way of using course of masquerading. Particularly, the binary is known as “lightdm”, mimicking the legit LightDM show supervisor generally discovered on Linux techniques. To boost the deception, the method is executed with command-line arguments resembling legit parameters – for instance,
lightdm –session baby 11 19 — in an effort to evade detection and mislead forensic analysts throughout post-compromise investigations.
These backdoors have been actively establishing connections to each the Raspberry Pi and the interior Mail Server.
As famous earlier, the processes have been disguised utilizing the Linux bind mount. Following that discovery, Group-IB added the method to the MITRE ATT&CK framework as “T1564.013 – Conceal Artifacts: Bind Mounts.”
Group-IB didn’t say the place the compromised switching gear was positioned or how attackers managed to plant the Raspberry Pi. The assault was detected and shut down earlier than UNC2891 was in a position to obtain its remaining aim of infecting the ATM switching community with the CakeTap backdoor.